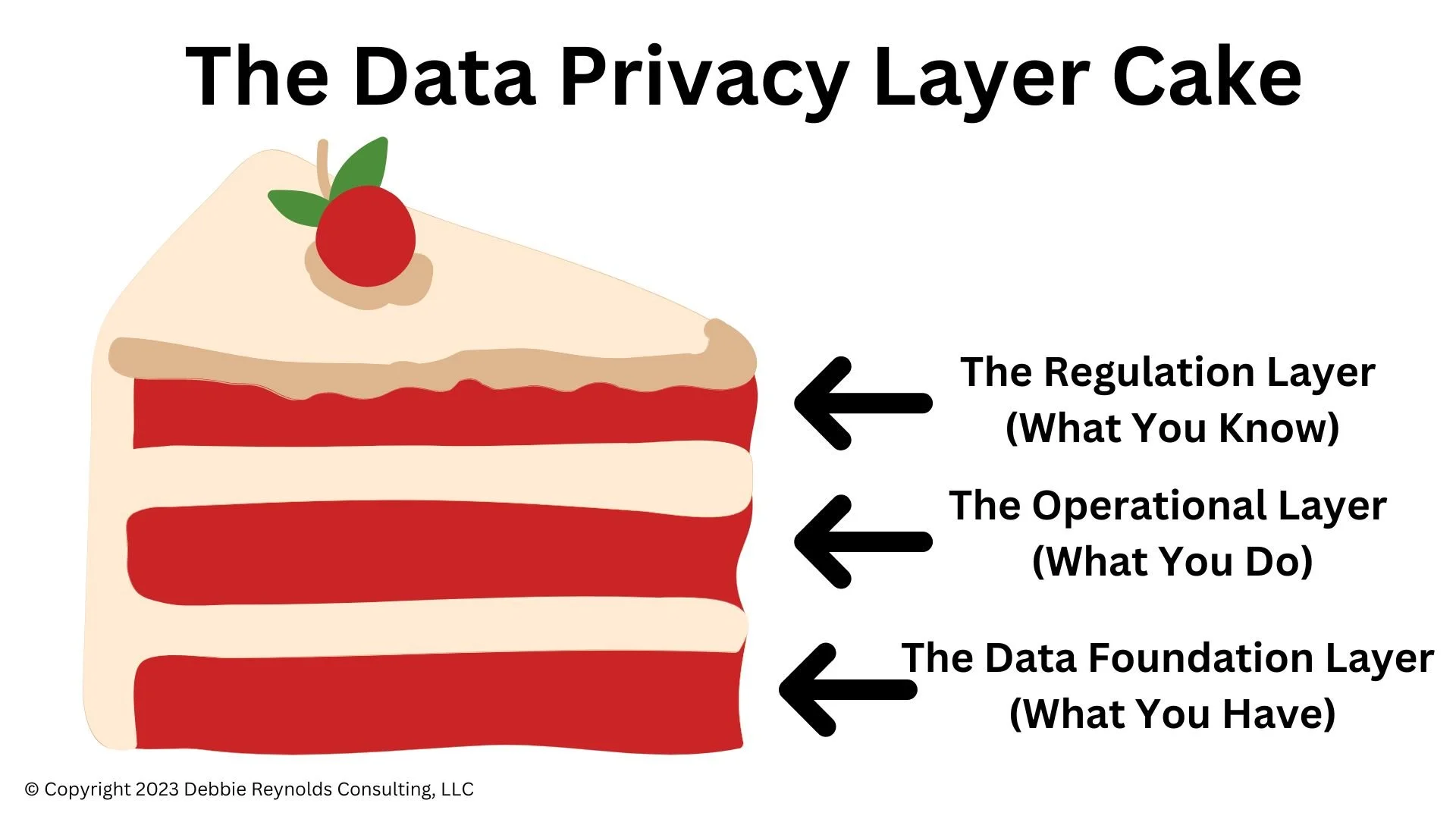
The Data Privacy Layer Cake: Examining Organizational Risk with a New Paradigm
The new frontier in our digital age and the rapidly evolving data landscape are making Data Privacy a top priority for organizations. From small businesses to multinational corporations, managing Data Privacy risks is a critical task that cannot be overlooked. The 'Data Privacy Layer Cake' model provides a comprehensive but easy-to-understand framework for identifying and addressing these risks. This model consists of three key layers: the Regulation Layer, the Operational Layer, and the Data Foundation Layer. This article discusses each layer and provides five actionable takeaways for organizations to effectively manage their Data Privacy risks using the 'Data Privacy Layer Cake'.
The Regulation Layer (What You Know)
The top layer of the Data Privacy Layer Cake signifies an organization's knowledge of existing laws and regulations. Understanding the ever-evolving landscape of Data Privacy regulations is vital to effective risk management. Here are five things organizations can do to manage risks at The Regulation Layer:
Advisory: Employ or consult with experts specialized in Data Privacy laws to guide your organization’s policies and ensure compliance.
Strategic Approach: Not all privacy laws apply to every business. Understand the specific regulations that are applicable to your business model, operations, and geographical locations. Adopt a strategic approach to align with these specific laws.
Policy Implementation: Update organizational policies as per the changes in the law. Implement these updated policies and align them with fundamental privacy principles across the organization.
Continuous Learning: Keep abreast of the latest legal and regulatory updates in Data Privacy from across the globe. This is crucial as businesses often deal with data across borders, subjecting them to international laws.
Education and Training: Regularly educate and train employees about the importance of adhering to Data Privacy laws and organizational policies.
The Operational Layer (What You Do)
The middle layer in the model deals with the actual handling of data within the organization. This is a critical layer where organizations face high risks due to potential operational mismanagement of data. Organizations get fined based on what they DO, not what they say they do. The operational layer is the one that is most often the hardest to change within organizations and creates the highest risks in organizations. Here are five things organizations can do to manage risks at the Operational Layer:
Data Lifecycle Management: Implement robust strategies to manage data throughout its lifecycle - creation, storage, usage, and disposal.
Data Protection Measures: Deploy data encryption, anonymization, and other security measures to prevent unauthorized access and data breaches.
Process Optimization: Regularly review and optimize data handling processes to eliminate unnecessary steps and unnecessary access that might increase risk exposure.
Emergency Response Plans: Develop and test incident response plans to handle potential data breaches swiftly and effectively.
Continuous Monitoring: Implement real-time monitoring of data handling activities to detect anomalies and take immediate corrective action.
The Data Foundation Layer (What You Have)
The bottom layer relates to the data itself, which is often a neglected aspect in many organizations. One of the biggest problems at this layer is that organizations too often have no clear view of what data they have or what additional risks exist as a result. Understanding what data you have can drastically reduce your Data Privacy risk exposure. Here are five things organizations can do to manage risks at the Data Foundation Layer:
Data Inventory: Conduct a thorough data inventory to identify all your data assets, including their sources and storage locations.
Data Classification: Categorize data based on its sensitivity and relevance to your business. This will allow for appropriate security measures and prioritize protection efforts.
Data Minimization: Practice data minimization, i.e., collect only the data you need and dispose of it responsibly when no longer required.
Privacy by Design: Implement the 'privacy by design' principles, which involve integrating Data Privacy measures from the initial design stage of systems and processes.
Data Quality Checks: Regularly update and clean data inventories to maintain accuracy, relevance, and compliance with Data Privacy laws.
The Data Privacy Layer Cake model provides a comprehensive and easy-to-understand view of the different aspects of Data Privacy Risk within organizations. The Regulation, Operational, and Data Foundation layer offers unique insights and challenges. The actionable takeaways provided for each layer in this model can help organizations identify their vulnerabilities at a high level, implement effective strategies, and consequently manage their Data Privacy risks more effectively to make Data Privacy a Business Advantage.